Bug Hunting Pt.1
I am participating in the above vulnerability disclosure program for the Defense Industrial Base.
The Defense Industrial Base Vulnerability Disclosure Program (DIB-VDP) Pilot is a 12-month voluntary event established collaboratively by DC3’s DoD Defense Industrial Base Collaborative Information Sharing Environment (DCISE), DoD Vulnerability Disclosure Program (DoD VDP), and the Defense Counterintelligence and Security Agency (DCSA).
Reconnaissance:
I will be conducting passive reconnaissance on each IP address using various command-line tools and OSINT techniques.
Passive reconnaissance is a method of gathering intelligence about a target without directly interacting with the target.
Keeping organized notes is critical to success.
I am using Microsoft Excel and Microsoft Notes for record keeping.

Whois
The first thing I want to do is run the IP addresses through whois to determine ownership and customer information.

Above is an example screenshot of what a whois report looks like.
I ran all 32 IPs through whois and documented all reports in my notes and xml.
The xml file is filling out nicely. Organization and neatness are critical when gathering intel and forming a profile.

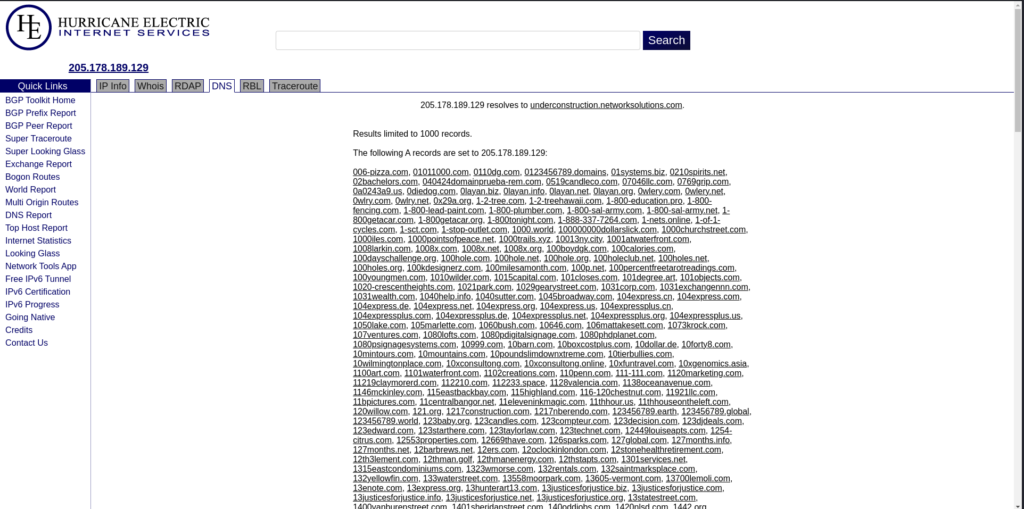
bgp.he.net
I am checking where each IP address resolves to by using the Hurricane Electric BGP Toolkit. The following is a screenshot of an example output.

DNSDumpster
After running “transporter.realstreet.com” && “inbound.realstreet.com” through DNSDumpster, I found 2 new IP addresses associated with these host names, or “A Records”.


nslookup
Reverse IP query using nslookup just to verify the findings.

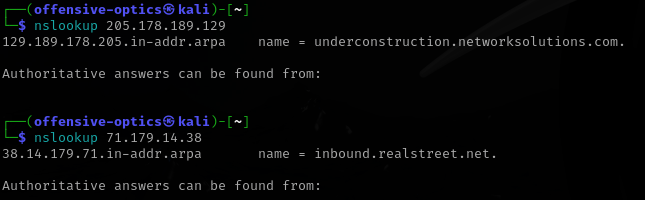
205.178.189.129 resolved to “underconstruction.networksolutions.com”
I queried that and was given a different IP address.

I recall from doing the DNS check on 205.178.189.129 that it was under-construction.
Shodan
Shodan is a search-engine that scans the internet looking for connected devices and systems.
All IPs will be checked for open ports, domains, and other general information.
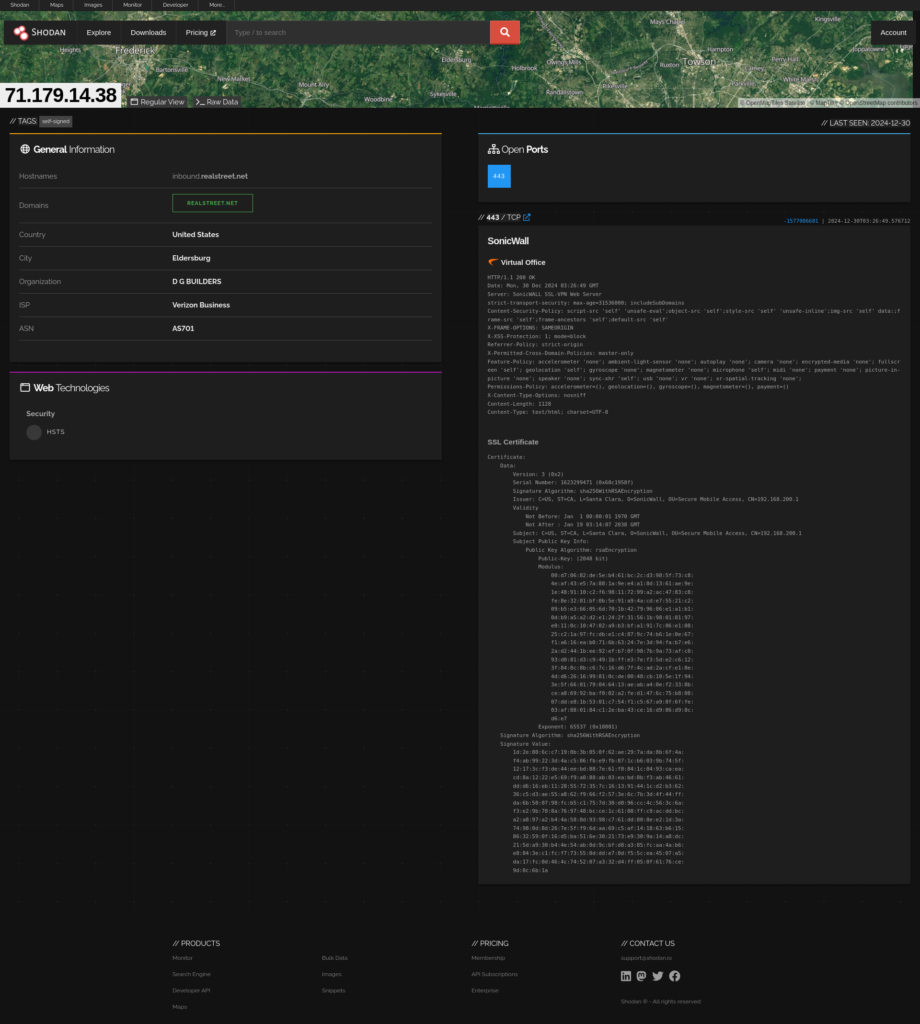
We see that 71.179.14.38 has an open port of 443, has a hostname of inbound.realstreet.net, and belongs to domain realstreet.net. Also Sonic Wall Virtual Office is running on 443.
I just completed running all IPs through Shodan.
I found a few open ports, hostnames, domains, and running services.
This is taking quite a while to do manually since I am working with over 30 IPs. There are automated tools to do this type of work but I prefer to first run manually then use automated tools.
Below is a screenshot of the spreadsheet I am creating. There is lots of good data has been found but there is still much more to find.
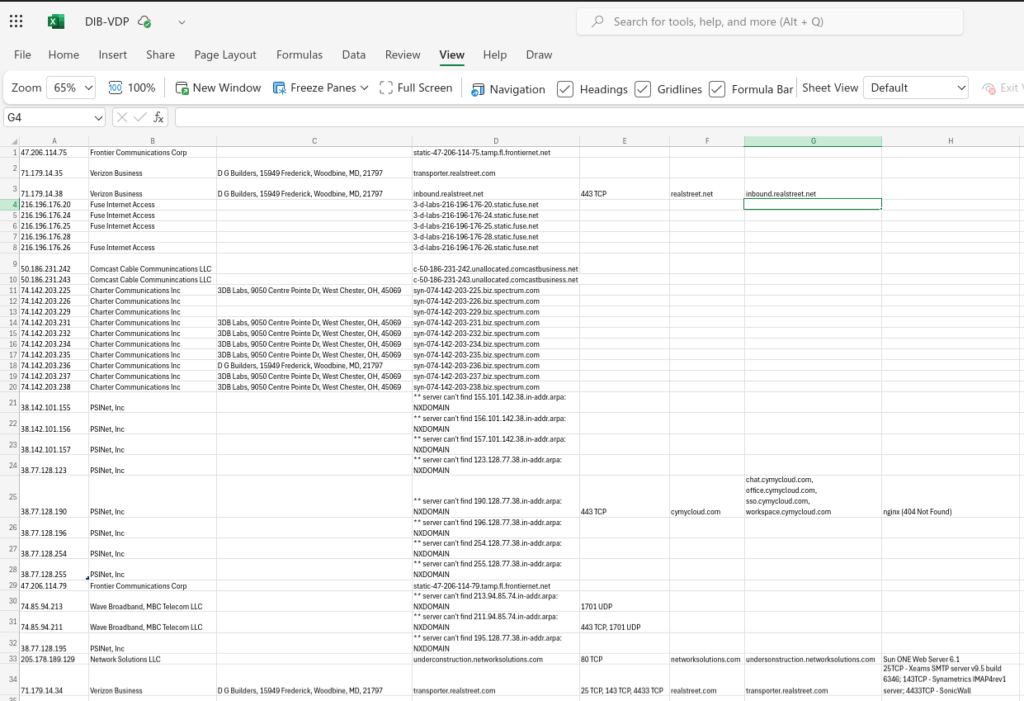
Now it is time to switch from passive recon to active recon. Passive reconnaissance does not directly interact with the target host but during active reconnaissance the target host is interacted with. For this I will use tools like Nmap, Spiderfoot, theHarvester, and Recon-NG. Plus, I will be checking to see if any of the internet-facing servers are protected by web application firewalls.
Spiderfoot
SpiderFoot is an open source intelligence (OSINT) automation tool that gathers information on targets by querying public data sources.
How it works:
You specify a target, choose which modules to enable, and SpiderFoot collects data to build an understanding of the target’s entities and relationships.
What it can do:
SpiderFoot can be used for reconnaissance or to gather information about what an organization has exposed online. It can target IP addresses, domain names, email addresses, phone numbers, and more.
Features:
SpiderFoot has over 200 modules that feed into each other to extract data. It can also integrate with other services like SHODAN, HaveIBeenPwned, and GreyNoise.

Due to the massive amount of information that is being output by Spiderfoot, I am going to focus only on this set of assets right now.
It is 8:54PM. Spiderfoot has been running since about 8:00AM. A few of the scans have completed but there are still 3 that are running. These 3 are huge. The scans that have completed so far have had around 300 elements found but these last 3 scans have 50,000+.
Massive!
Thankfully, Spiderfoot exports in csv file format.
It offers excel exports but it wasn’t working with my web-based Excel so I have to go with the csv and use libreoffice for viewing.
I’m going through each csv and transferring relevant information into Excel. This is very time consuming but fun.
Filed under: Uncategorized - @ January 11, 2025 8:08 AM