Testing Password Strength&& Hacking A WIFI Network
Environment:
I have used a mobile hotspot to create the target WiFi network. On this network, I have connected a laptop.
Scenario:
I will be using the Hak5 WiFi Pineapple Mark VII to obtain the 4-way handshake for the target SSID, use Hashcat to brute force the password hash, use the cracked password hash to connect to the target network, then use Nmap to scan the network for any endpoints that could be potentially interesting targets. (The laptop connected to the target network will simulate a potential target.)

WiFi Pineapple Mark VII with 5G add-on adapter
Historical Password Analysis Considerations:
The average passwords ranges in 7 to 9 characters in length.
Women prefer personal names in their passwords, and men prefer hobbies.
If a number, it’s usually a 1 or 2, sequential, and will likely be at the end.
If more than one number it will usually be sequential or personally relevant.
If a capital letter, it’s usually the beginning, followed by a vowel.
Test Password:
The password used is 9 characters in length. It has 1 capital letter, 6 – 7 lowercase letters, 1 or 2 numerical values, and 1 special character.
WiFi Pineapple:
To access the GUI, I have to enter the credentials.
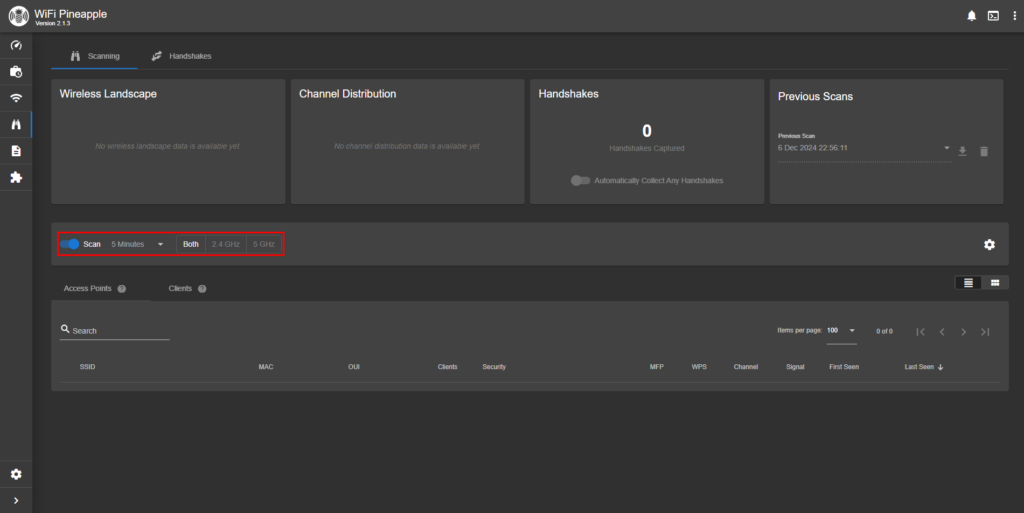
After logging in, I navigated to the Recon page. From here, I will run a 5 minute scan to identify all existing wifi networks within the range of the Pineapple.
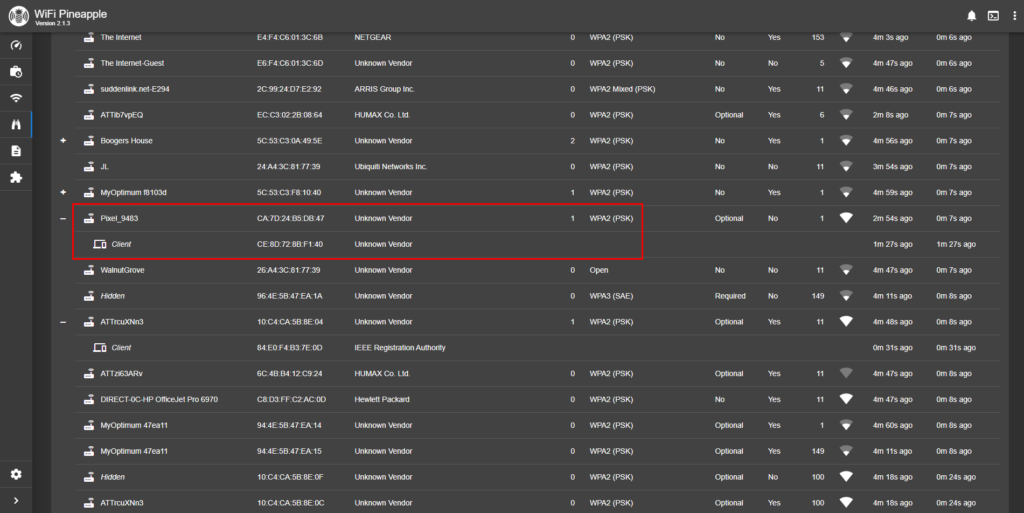
The scan revealed 43 wifi access points (SSIDs) within range. The target SSID name is “Pixel_9483”. As can be seen within the red boxed- in areas, there is a client connected to the target SSID. That client is a laptop. I want to scan that laptop.
After clicking on the target SSID, a drop-down menu appears on the right side of GUI. From this menu, I will choose “Capture WPA Handshakes” then press “Start Capture” in pop-up screen. This will allow the Pineapple to record the 4-way password authentication process and save it as a PCAP or Hashcat file. I need the Hashcat format file.
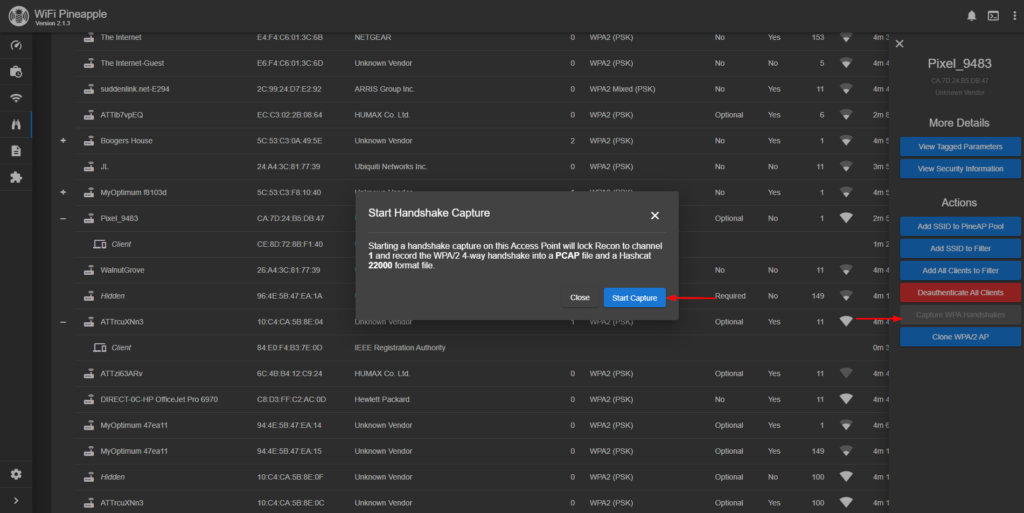
After starting handshake capturing, it is time to begin attacking the target with deauthentication packets. This will force all clients on the target SSID to have to reconnect, essentially forcing a 4-way handshake to take place.
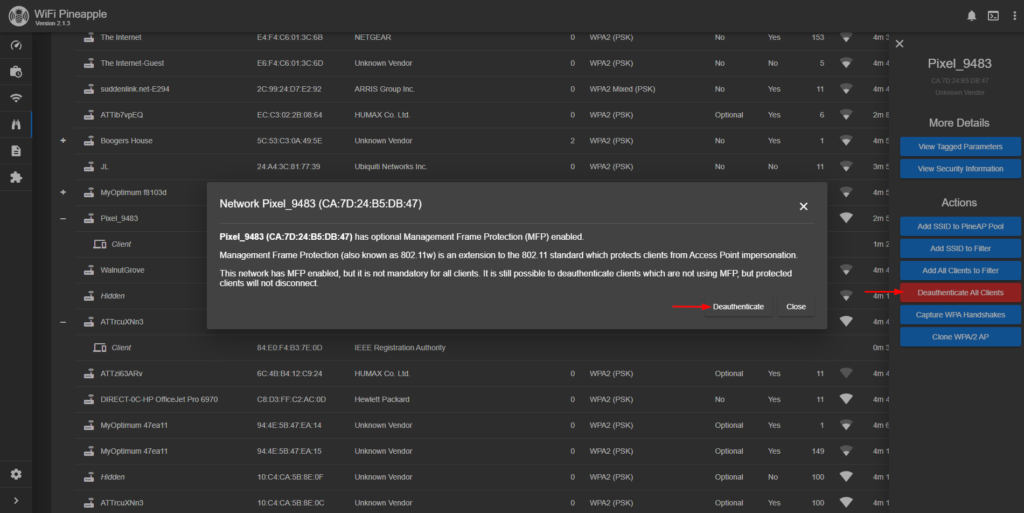
Within a matter of maybe 5 minutes, the Pineapple captured the 4-way handshake for the target SSID.
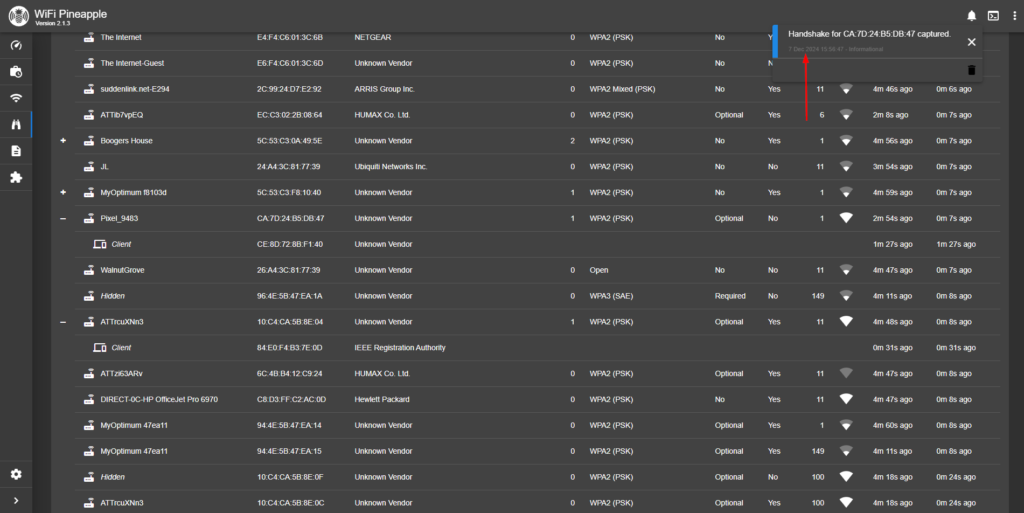
From here, I download the Full Hashcat file type.

The 4-way handshake Hashcat format file has been downloaded.

Windows CLI:
After opening up the Windows Command-line, I navigated to the hashcat-6.2.6 directory. From here, I will be executing commands for Hashcat to brute force the password hash file. For ease of access, I placed the Hashcat file into the hashcat-6.2.6 directory.
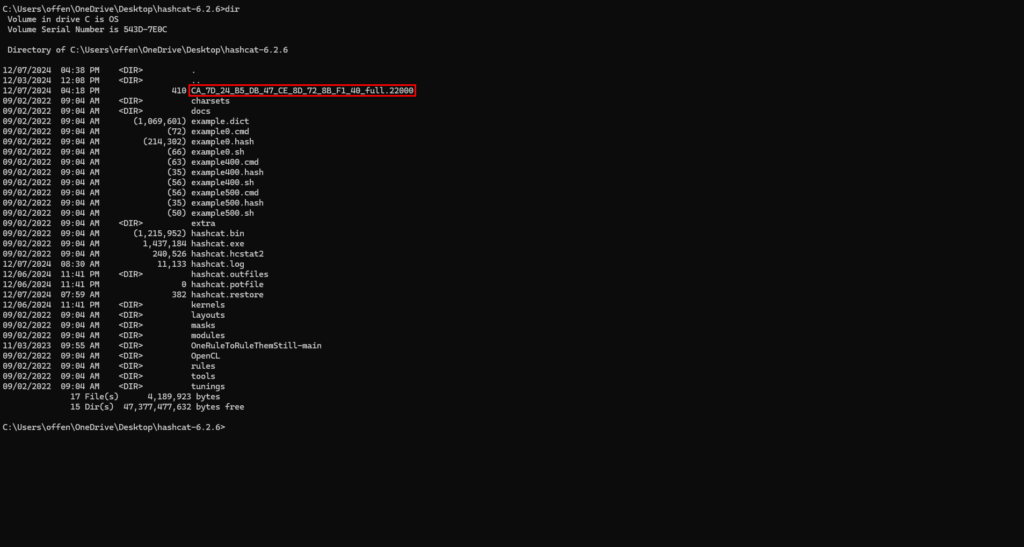
The screenshot below is the command used to brute force the password using Hashcat. I will explain the command. “hashcat” calls the executable, “-a” is the attack type flag, “3” is the brute force flag, “-m” is the hash mode flag, “22000” is the mode for WPA-PBKDF2-PMKID+EAPOL hash files, “-1 ?l?d ?u?l?l?l?l?l?1?d?s” is the brute force custom charset I am using to test the target password hash. It takes into account all of the historical password analysis considerations from earlier.
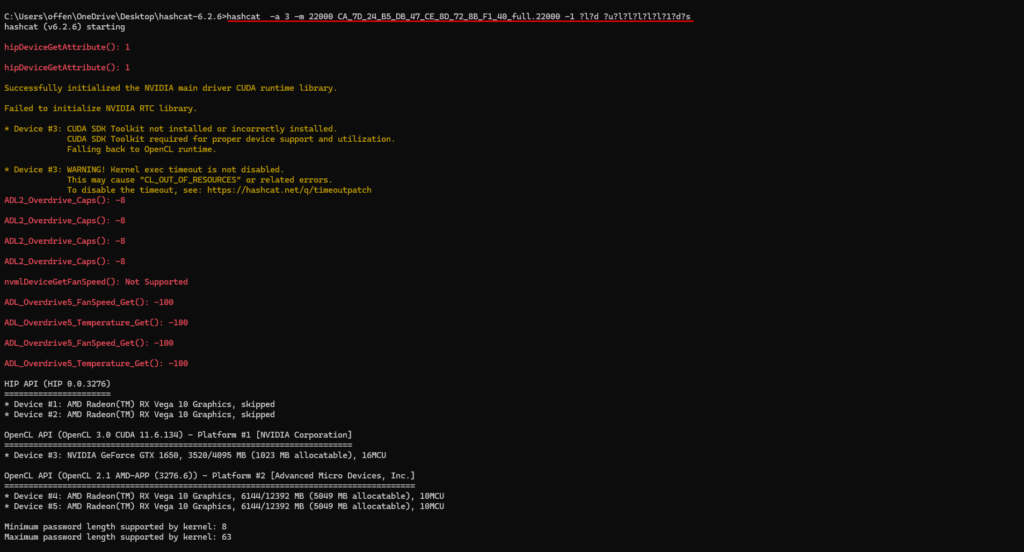
So far, Hashcat has been running for 13 hours and 48 minutes. I know that the password will eventually be cracked using the brute force and custom charset method but I decided to pause it and try another method of attack.
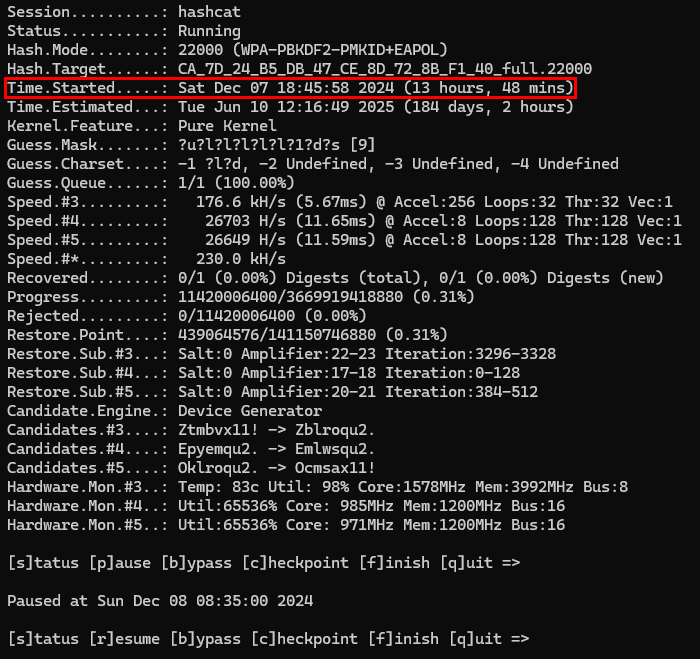
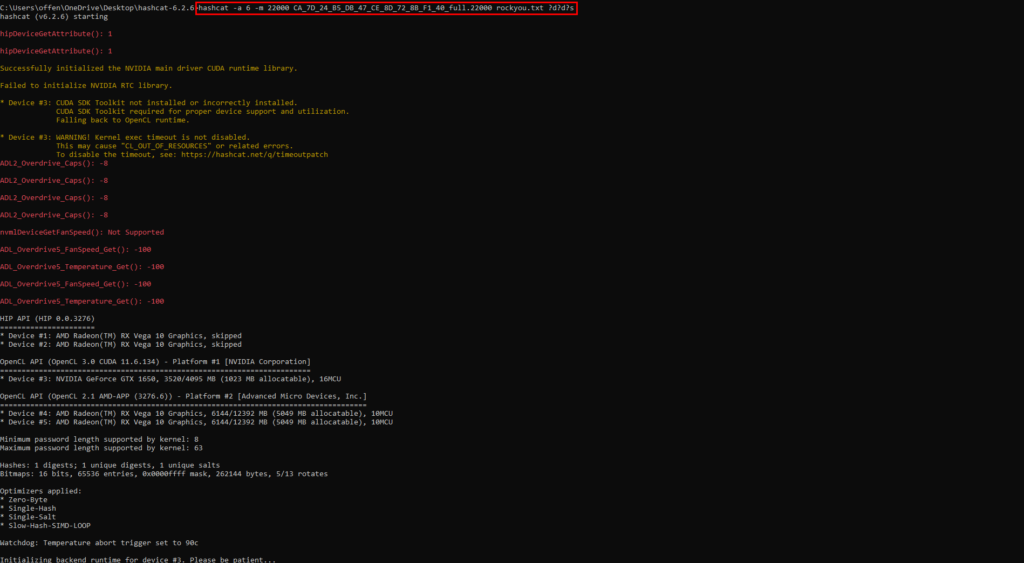
I downloaded the rockyou.txt wordlist and placed it in the hashcat directory. The attack mode I will be using is “Hybrid Wordlist + Mask”. That means that the wordlist will be used and that on the right of the words will be added the digits and special charcter charsets. I have a feeling that this method of attack will produce a positive result in a shorter period of time than the straight brute force method.
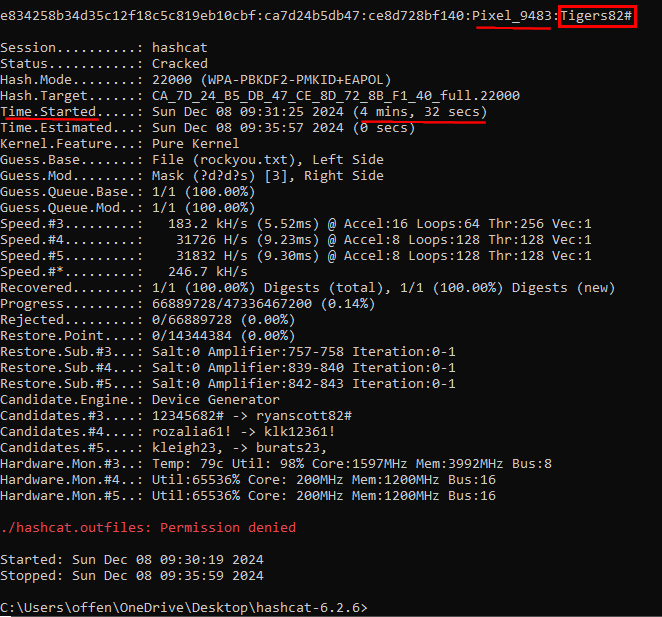
Alright! Well, that didn’t take long at all. 4 minutes and 32 seconds to crack the hash using the rockyou.txt wordlist and mask attack method. As can be seen in the red box, Pixel_9483’s password is “Tigers82#”. Be carful using this type of password format as it can be easily figured out.
Very good! Now it is time to hop back onto the WiFi Pineapple Mark VII to connect to the target SSID and scan the network.
WiFi Pineapple Mark VII:
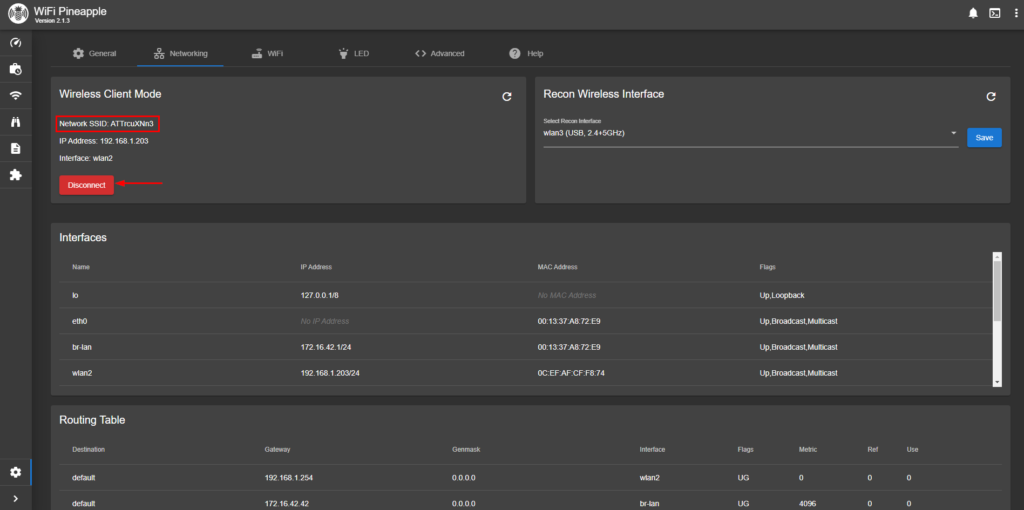
Back in the Pineapple GUI, I navigated to the Networking page. As seen in the red box, I am currently connected to the network SSID “ATTrcuXNn3”. I will disconnect from this network and connect to Pixel_9483.
After I chose the correct SSID and entered the password “Tigers82#”, I clicked connect.
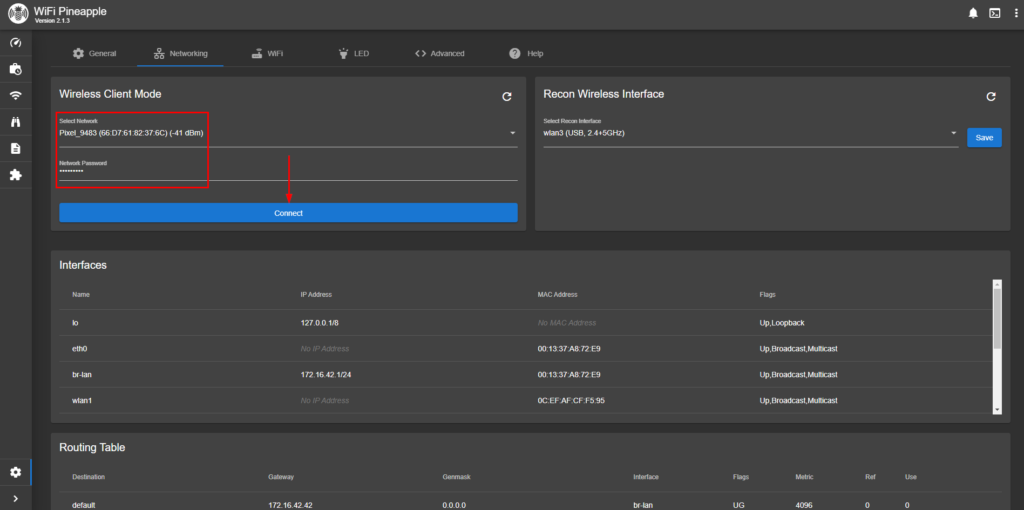
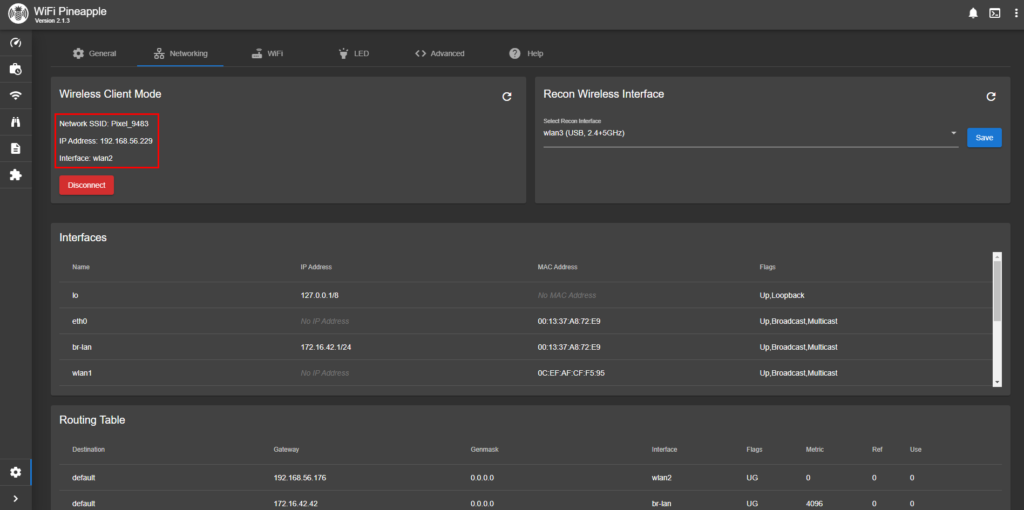
I am now connected to the target SSID and have been assigned the IP Address of 192.168.56.229. It is now time to open up the built-in Linux terminal to use the network scanning tool Nmap to scan for any endpoints on the compromised wireless network.
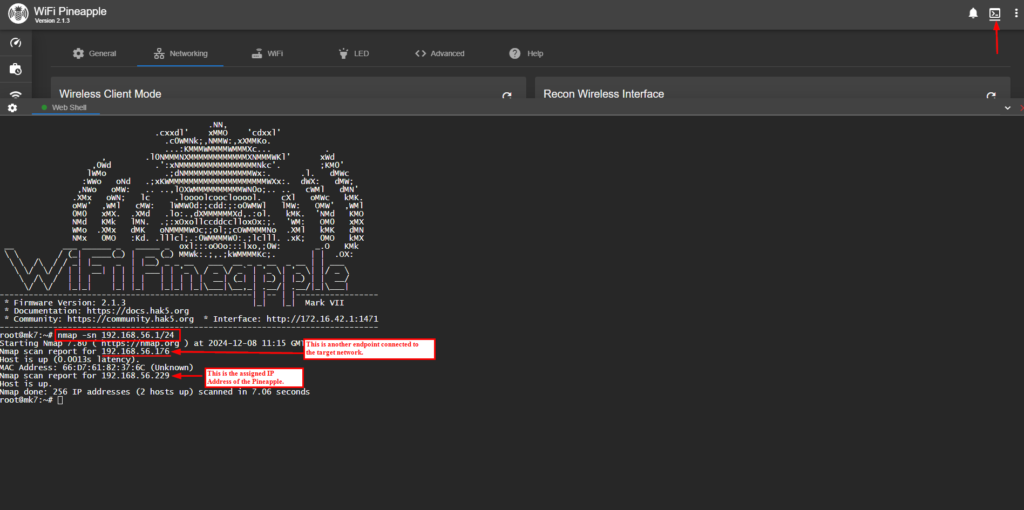
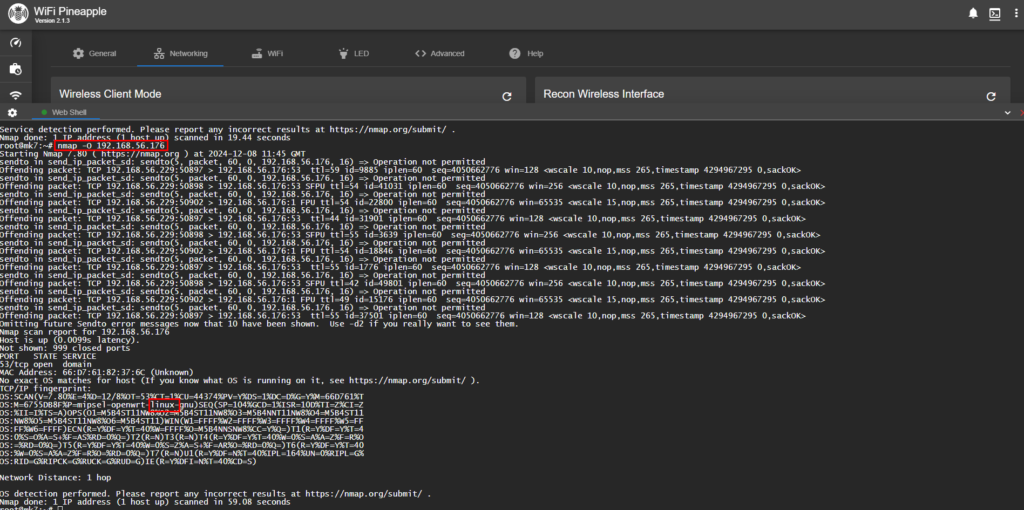
After clocking the terminal icon in the upper right corner, I entered the Nmap command to scan the network for all connected endpoints. The scan reported 2 endpoints. One is the Pineapple and the other is the laptop that I am wanting to scan for open ports, OS and Protocol versions.
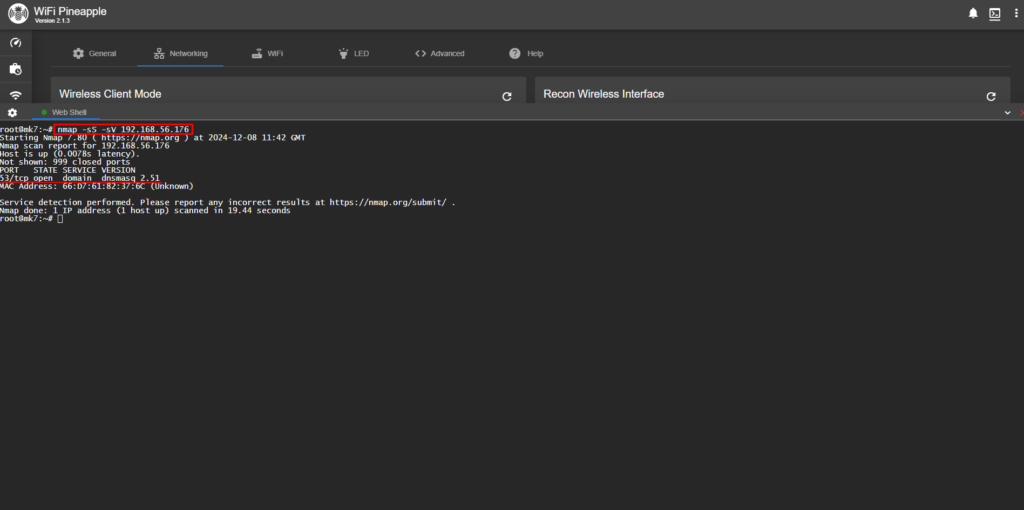
I entered the Nmap command to run an SYN scan to check for open ports and an Version scan to show what version the Protocols are using. As shown in the screenshot, Port 53 (DNS) is open and the service version is dnsmasq 2.51.
Lastly, I ran an OS (Operating System) scan on the target IP. The scan produced inconclusive results but as can seen in the lower red box, the scan did pick up that it was Linux but could not match the exact OS. (Linux PopOS is running on the laptop.)
In Conclusion:
The Hak5 Wifi Pineapple Mark VII allows for fast and easy capturing of 4-way handshakes. Hashcat is the best hash cracking program since it allows for the use of GPUs. This certainly speeds up the process. Also, even a 9 character password can be easily cracked if using the correct attack modes. Be careful out there!
Filed under: Uncategorized - @ December 8, 2024 11:55 AM